Information Technology Intelligence Consulting Corp. 2022 Editorial Calendar
March 2022: ITIC Sexual Harassment, Gender Bias and Pay Equity Survey
Description: ITIC’s third annual “Sexual Harassment, Gender Bias and Pay Equity Gap,” independent Web survey will poll approximately 1,200 to 1,500 women professionals worldwide across 47 different industries, with a special emphasis on STEM disciplines. The survey focuses on three crucial areas of workplace discrimination: Sexual Harassment, Gender Bias and Unequal Pay. It polls women professionals, ranging from interns to retirees on their workplace experiences and how they coped.
April: 2022 Hourly Cost of Downtime
Description: Downtime impacts every aspect of the business. It can disrupt operations and end user productivity, result in data losses and raise the risk of litigation. Downtime can also result in lost business and irreparably damage a company’s reputation. The cost of downtime continues to increase as do the business risks. ITIC’s 2019 Hourly Cost of Downtime survey found an 85 % majority of organizations now require a minimum of 99.99% availability. This is the equivalent of 52 minutes of unplanned outages related to downtime for mission critical systems and applications or just 4.33 minutes of unplanned monthly outage for servers, applications and networks. This survey will once again poll corporations on how much one hour of downtime costs their business – exclusive of litigation, civil or criminal penalties. ITIC will also interview customers and vendors across 10 key vertical markets including: Banking/Finance; Education; Government; Healthcare; Manufacturing; Retail; Transportation and Utilities. The Report will focus on the toll that downtime extracts on the business, its IT departments, its employees, its business partners, suppliers and its external customers. This report will also examine the remediation efforts involved in resuming full operations as well as the lingering or after-effects to the corporation’s reputation as the result of an unplanned outage.
April 2022: ITIC 2022 Security Trends and Threats in Datacenters, Cloud and the Network Edge
Description: Security, security, security! Security impacts every aspect of computing and networking operations in the Digital Age. And it’s never been more crucial as businesses, schools, government workers and consumers are working at home amidst the ongoing Nouvel and damaging security hack impacting the lives of millions of consumers and corporations. This Report will utilize the latest ITIC independent survey data to provide an overview of the latest trends in computer security including the latest and most dangerous hacks and what corporations can do to defend their data assets. Among the topics covered:
- Security threats in the age of COVID-19
- The most prevalent type of security hacks
- The percentage of corporations that experienced a security hack
- The duration of the security hack
- The severity of the security hack
- The cost of the security hack
- Monetary losses experienced due to security breaches
- Lost, damaged, destroyed or stolen data due to a security breach
- The percentage of time that corporations spend securing their networks and data assets
- Specific security policies and procedures companies are implementing
- The issues that pose the biggest threats/risks to corporate security
May/June 2022: ITIC 2022 Global Cloud Reliability, Security and Usage Trends Survey
Description: Public, private and hybrid cloud adoption is rising exponentially, with over 20% CAG anticipated between 2022 and 2025. Corporations from SMEs to the largest multinational global enterprise customers are likewise increasing cloud/IaaS spending. By 2025, enterprise stakeholders worldwide will spend well over $200 billion in cloud products, services, security and storage. As organizations’ cloud usage grows, the reliability, availability and security of the various cloud hosting platforms is crucial. ITIC’s forthcoming Global Cloud Reliability, Security and Usage Trends Survey polls C-Suite executives, IT and security managers businesses in the top 15 vertical market segments worldwide on the reliability, uptime and security of the top cloud platforms including: Amazon Web Services (AWS); Microsoft Azure; Alibaba Group; Google Cloud Platform; IBM Cloud; Oracle Cloud; CenturyLink; Rackspace; OVHCloud; Digital Ocean and others. This independent Web-based survey will query cloud customers the amount of downtime experienced by individual cloud platforms including: the frequency, duration, severity and security issues associated with unplanned outages. It will also poll corporate enterprises on their satisfaction with technical service and support.
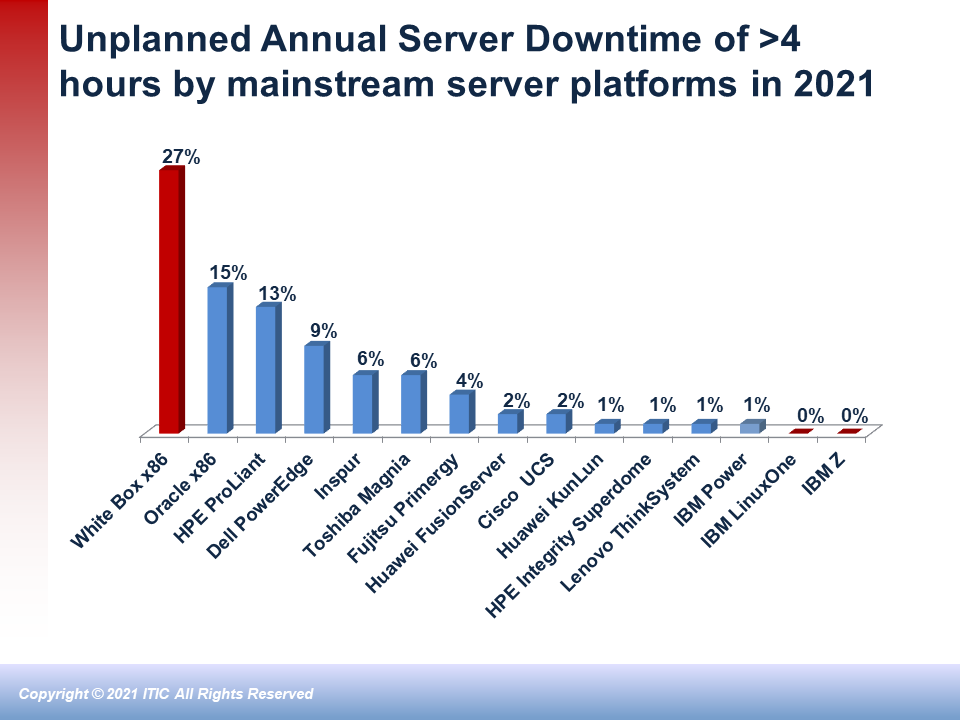
June 2022: ITIC 2022 Global Server Hardware and Server OS Reliability Survey
Description: ITIC’s 14th Annual Global Server Hardware, Server OS Reliability polls businesses on the reliability, uptime and management issues involving the inherent reliability of over one dozen different server hardware platforms and server operating system. The poll queries corporations on the frequency, the duration, the severity and the causes associated with Tier 1, Tier 2 and Tier 3 outages. The results of this independent, non-vendor sponsored survey will provide businesses with the information they need to determine the TCO and ROI of their individual environments. The survey will also enable the server OS and server hardware vendors to see how their products rate among global users ranging from SMBs with as few as 25 people to the largest global enterprises with 100,000+ end users.
The 2022 ITIC Global Reliability Survey has also been updated and expanded to include questions on server-based reliability in private, public and hybrid clouds as well as security and interoperability issues. As always, ITIC’s Reliability survey will delve into the following issues:
- Component level failure data comparisons between a wide range of server vendors including a comparison of IBM Z and IBM Power Servers and Intel-based x86 servers such as Cisco, Dell, Fujitsu, HPE, Huawei, Inspur, Lenovo, Oracle and unbranded white box servers.
- Percentage of component level failure data comparisons by vendor according to age (e.g. new to three months; three to six months; six months to 1 year; 1 to 2 years; 2 to 3 years; 3 to 4 years; 4 to 5 years; over five years).
- Which component parts fail and frequency of failure
- A percentage breakout of server parts failures for parts such as hard disk drives(HDD), processors, memory, power components, fans, or other
- Where available, how the component failed, e.g., memory multi-bit errors, HDD read failures, processor L1/L2 cache errors, etc.
August: 2022 IoT Deployment and Usage Trends Survey and Report
Description: The Internet of Things (IoT) is one of the hottest technologies. This ITIC Report will poll corporations on the business and technical challenges as well as the costs associated with IoT deployments. This IoT Report will also examine the ever present security risks associated with interconnected environments and ecosystems. ITIC’s IoT 2022 Deployment and Usage Trends Survey will also query global businesses on a variety of crucial issues related to their current and planned Internet of Things (IoT) usage and deployments such as how they are using IoT (e.g. on-premises versus Network Edge/Perimeter deployments); the chief benefits and biggest challenges and impediments to IoT upgrades. Vendors profiled for this report will include: AT&T, AWS, Bosch, Cisco, Dell, Fujitsu, EuroTech, General Electric (GE), Google, Hitachi, Huawei, IBM, Intel, Microsoft, Particle, PTC, Qualcomm, Samsung, SAP, Siemens, Software AG, and Verizon.
August/September: ITIC 2022 Global Server Hardware Server OS Reliability Survey Mid-Year Update
Description: This Report is the Mid-year update of ITIC’s Annual Global Server Hardware, Server OS Reliability Survey. Each year ITIC conducts a second survey of selected questions from its Annual Reliability poll. ITIC also conducts new interviews with C-level executives and Network administrators to get detailed insights on the reliability of their server hardware and operating system software as well as the technical service and support they receive from their respective vendors. ITIC will also incorporate updated PowerPoint slides and statistics to accompany the report.
October/November: AI, Machine Learning and Data Analytics Market Outlook
Description: This Report will examine the pivotal role that AI, Machine Learning and IoT-enabled predictive and prescriptive Analytics plays in assisting businesses sort through the data deluge to make informed decisions and derive real business value from their applications. AI and Machine Learning take Data Analytics to new levels. They can help businesses identify new product opportunities and also uncover hidden risks. Machine intelligence is already built into predictive and prescriptive analytics tools, speeding insights and enabling the analysis of vast probabilities to determine an optimal course of action or the best set of options. Over time, more sophisticated forms of AI will find their way into analytics systems, further improving the speed and accuracy of decision-making. Rather than querying a system and waiting for a response, the trend has been toward interactivity using visual interfaces. In the near future, voice interfaces will become more common, enabling humans to carry on interactive conversations with digital assistants while watching the analytical results on a screen. Analytics makes businesses more efficient; it enables them to cut costs and lower ongoing operational expenditures. It also helps them respond more quickly and agilely to changing market conditions – making them more competitive and thus driving top line revenue in both the near term and long term strategic sales. Vendors Profiled: AppDynamics, BMC, Cisco, IBM, Microsoft, Oracle, SAP and SAS. It also discusses how non-traditional vendors in the carrier and networking segments e.g. Dell/EMC, GE, Google, Verizon and Vodafone have fully embraced AIOps and analytics via partnerships, acquisitions and Research and Development (R&D) initiatives and have moved into this space and challenged the traditional market leaders. And it will provide an overview of the latest Mergers and Acquisitions (M&A) and their impact on the Analytics industry.
December: ITIC 2022 Technology and Business Outlook
Description: This Report will be based on ITIC survey results that poll IT administrators and C-level executives on a variety of forward looking business and technology issues for the 2022 timeframe. Topics covered will include: Security, IT staffing and budgets; application and network infrastructure upgrades; hardware and software purchasing trends and cloud computing.
Survey Methodology
ITIC conducts independent Web-based surveys that contain multiple choice and essay questions. In order to ensure the highest degree of accuracy, we employ authentication and tracking mechanisms to prohibit tampering with the survey results and to prohibit multiple votes by the same party. ITIC conducts surveys with corporate enterprises in North America and in over 25 countries worldwide across a wide range of vertical markets. Respondents range from SMBs with 25 to 100 workers to the largest multinational enterprises with over 100,000 employees. Each Report also includes two dozen first person customer interviews and where applicable, vendor and reseller interviews. The titles of the survey respondents include:
- Network administrators
- VPs of IT
- Chief information officers (CIOs)
- Chief technology officers (CTOs)
- Chief executive officers (CEOs)
- Chief Information Security Officers (CISOs)
- Chief Marketing Officers (CMOs)
- Consultants
- Application developers
- Database Administrators
- Telecom Manager
- Software Developer
- System Administrator
- IT Architect
- Physical Plant Facilities Manager
- Operations Manager
- Technical Lead
- Cloud Managers/Specialists
- IoT Manager
- Server Hardware/Virtualization Manager
ITIC welcomes input and suggestion from its vendor and enterprise clients with respect to surveys, survey questions and topics for its Editorial Calendar. If there are any particular topics or questions in a specific survey that you’d like to see covered, please let us know and we will do our best to address it.
About Information Technology Intelligence Corporation (ITIC)
ITIC, founded in 2002, is a research and consulting firm based in suburban Boston. It provides primary research on a wide variety of technology topics for vendors and enterprises. ITIC’s mission is to provide its clients with tactical, practical and actionable advice and to help clients make sense of the technology and business events that influence and impact their infrastructures and IT budgets. ITIC can provide your firm with accurate, objective research on a wide variety of technology topics within the network infrastructure: application software, server hardware, networking, virtualization, cloud computing, Internet of Things (IoT) and Security (e.g. ransom ware, cyber heists, phishing scams, botnets etc.). ITIC also addresses the business issues that impact the various technologies and influence the corporate business purchasing decisions. These include topics such as licensing and contract negotiation; GDPR; Intellectual Property (IP); patents, outsourcing, third party technical support and upgrade/migration planning.
For more information visit ITIC’s website at: www.itic-corp.com.
To purchase or license ITIC Reports and Survey data contact: Fred Abbott
Email: fhabbott@valleyviewventures.com;
Valley View Ventures, Inc.
Phone: 978-254-1639
Information Technology Intelligence Consulting Corp. 2022 Editorial Calendar Read More »